| CPC H04L 63/1466 (2013.01) [G06N 3/08 (2013.01); G06N 5/025 (2013.01); H04L 63/029 (2013.01); H04L 63/1416 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A method, comprising:
storing threat information in an adversarial technique framework data structure using a framework and a data model of a set of known threats based on tools, tactics or procedures used by adversary groups, software, techniques, malware or campaigns;
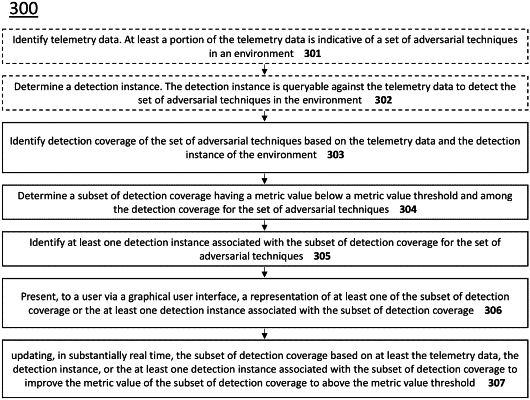
electronically receiving a set of telemetry data from one or more networked components forming part of a network infrastructure, wherein the telemetry data is indicative of adversarial techniques, and wherein the networked components comprise one or more hardware or software components for monitoring a security state on a computer network;
automatically storing in a computerized data store one or more of security product configuration information, detection logic, and the telemetry data, wherein the security product configuration information comprises information about the networked components;
generating scores for the set of known threats;
determining one or more prioritized mitigation recommendations based on at least the scores for the threats in the set of known threats; and
presenting to a user via a graphical user interface the one or more prioritized mitigation recommendations, wherein determining the one or more mitigation recommendations further comprises:
storing a set of mitigations mapped for association with the set of known threats, detection logic, and telemetry data;
mapping the stored threat information for the set of known threats against the telemetry data to identify one or more security coverage gaps; and
determining the one or more mitigation recommendations based on the one or more identified security coverage gaps.
|