| CPC H04L 63/102 (2013.01) [G06F 9/451 (2018.02); G06F 9/54 (2013.01); G06F 16/13 (2019.01); G06F 16/23 (2019.01); G06F 16/2379 (2019.01); G06F 16/245 (2019.01); G06F 16/248 (2019.01); G06F 21/6218 (2013.01); G06Q 40/03 (2023.01); H04L 63/062 (2013.01); H04L 63/083 (2013.01); H04L 63/0861 (2013.01); H04L 63/0884 (2013.01); H04L 63/18 (2013.01); H04L 67/306 (2013.01); H04L 2463/121 (2013.01)] | 20 Claims |
|
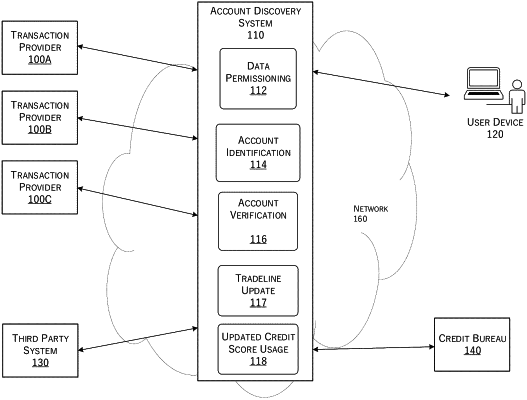
1. A method performed by a computing system having one or more hardware computer processors and one or more non-transitory computer readable storage devices storing software instructions executable by the computing system to perform the method, the method comprising:
receiving, from a user computing device of a user, a selection of a third-party entity;
identifying an Application Programming Interface (API) token associated with the third-party entity;
transmitting the API token to a system in electronic communication with the third-party entity;
receiving, via the system, indicators of one or more accounts of the user with the third-party entity;
receiving, from the user computing device, a selection of an account of the one or more accounts;
accessing, via a secure communication session initiated with the API token, a plurality of data items of the selected account of the user with the third-party entity;
transmitting first user interface data to the user computing device, the first user interface data configured to depict a first user interface on a display of the user computing device, the first user interface including one or more interactive elements selectable to indicate authorized uses of the data items by the computing system;
receiving, from the user computing device, a selection of authorized uses of at least a subset of the data items; and
in response to receiving the selection of authorized uses, selectively sharing at least the subset of the data items with a computing device for the one or more authorized uses, wherein the computing device is different than the user computing device and the computing system.
|