| CPC H04L 63/102 (2013.01) [G06F 21/31 (2013.01); H04L 63/108 (2013.01); G06F 2221/2103 (2013.01)] | 17 Claims |
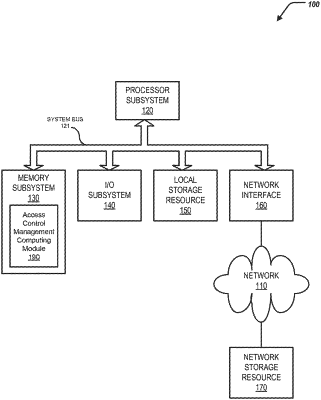
|
1. A computer-implemented method of providing access control to distributed resources, the method comprising:
storing, at a computing dock coupled to an information handling system, a local access database indicating verified credentials of one or more users;
receiving, at the computing dock, a request for access to a resource coupled to the computing dock;
providing, in response to the request for access, an authentication request to an authentication system;
in response to the authentication request, providing, by the computing dock, an authentication challenge to the information handling system;
receiving, at the computing dock and in response to the authentication challenge, user credentials at the authentication system;
verifying, at the authentication system, the user credentials against the local access database;
providing, based on the verified user credentials, an authorization token to the first device; and
allocating, based on the authorization token, access to the resource to the information handling system.
|