| CPC G06V 20/52 (2022.01) [G06F 21/6209 (2013.01); G08B 21/00 (2013.01); G06F 2221/2141 (2013.01); G06V 2201/07 (2022.01)] | 20 Claims |
|
1. A system, comprising:
a remote monitoring computing system comprising:
a data store;
at least one processor; and
at least one computer-readable medium storing a plurality of instructions that, when executed by the at least one processor, cause the at least one processor to:
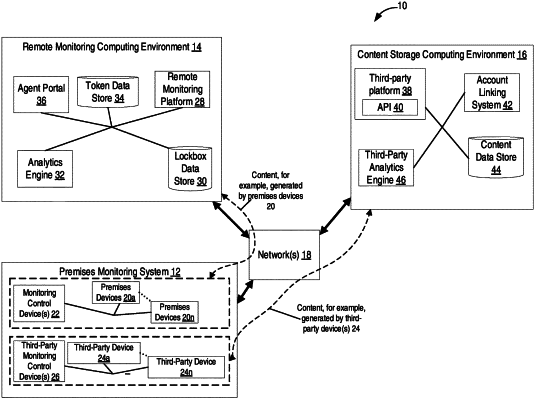
receive an alarm signal from a premises monitoring system that is configured to monitor a premises, the alarm signal being associated with an alarm event at a premises monitored by the premises monitoring system;
in response to the alarm signal, cause transmission of a notification of the alarm event to a content storage computing system, the content storage computing system comprising a cloud data storage system;
receive, in response to the notification, metadata corresponding to a video provided by a camera located at the premises and stored in the cloud data storage system;
determine that the metadata corresponding to the video indicates that a person was detected in the video;
in response to determining that the metadata corresponding to the video indicates that the person was detected in the video, download the video from the content storage computing system;
store the video in the data store of the remote monitoring computing system; and
enforce an access control policy on the video in the data store, the access control policy restricting access to the video in the data store based on time and a plurality of roles of a plurality of users of the remote monitoring computing system, the access control policy comprising:
a first tier that permits a monitoring agent assigned to the alarm event to access the video for only a first period of time;
a second tier that permits a supervisor of the monitoring agent to access the video for only a second period of time, the second period of time encompassing the first period of time and being longer than the first period of time; and
a third tier that permits a designated administrator to access the video for only a third period of time, the third period of time encompassing the first period of time and the second period of time, the third period of time being longer than the first period of time and the second period of time; and
cause the video to be deleted from the data store after the third period of time.
|