| CPC G06F 9/544 (2013.01) | 8 Claims |
|
1. An information creating device comprising:
at least one processor; and
a memory storing a program comprising instructions that, when executed by the at least one processor, cause the device to perform a set of operations to:
activate a first application;
acquire, using an operating system associated with the first application while activating the first application, a file path list, wherein the file path list represents a set of file paths associated with files being accessed by another file while activating the first application, the file path list includes:
a configuration file path associated with a configuration file of the first application,
a first file path associated with a first file being accessed from a second file, and
a second file path associated with the second file accessed by the configuration file;
trace, starting from the configuration file associated with the first application, the second file and the first file as a series of accessed files according to the file path list;
identify, based on a result of the trace of the configuration file and the second file, whether access to first file is caused by activation of the first application;
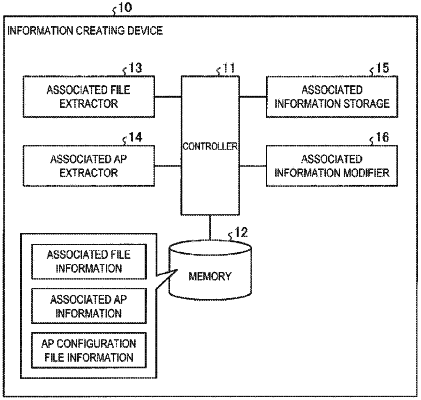
extract, based on a result of identifying whether the access to the first file is caused by activation of the first application, the first file as an associated file of the associated file information associated with the first application, wherein the associated file is accessed in connection with the activation of the first application;
deactivate, based at least on the extraction of the first file, the first application;
identify a second application, wherein the second application transmits and receives data to and from the first application while activating the first application;
store, in a memory, the associated file information associated with the first application;
store, in the memory, associated application information associated with the first application, wherein the associated application information indicates the second application that transmits and receives the data to and from the first application while activating the first application;
determine, based on anomaly in the association file information and the associated application information, a state of integrity associated the first application, wherein the state of integrity indicates whether there is anomaly in activating the first application; and
execute, based on the determined state of integrity without anomaly, operation of the first application.
|