| CPC G06F 21/87 (2013.01) [G06F 21/35 (2013.01); G06F 21/606 (2013.01); G06F 21/6218 (2013.01)] | 7 Claims |
|
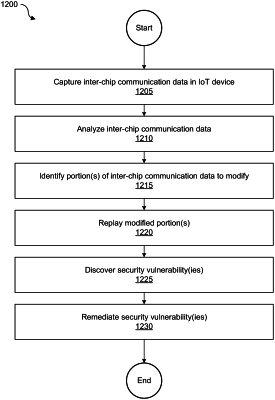
1. A computer-implemented method, comprising:
capturing inter-chip communication data in an Internet of Things (IoT) device;
identifying a communication direction, an address format, a flow control, a communication timing, and a communication structure associated with the inter-chip communication;
based on the communication direction, the address format, the flow control, the communication timing, and the communication structure, identifying one or more portions of the inter-chip communication data that require modification so that the inter-chip communication data can be replayed;
identifying one or more security vulnerabilities based on the modification and the replaying; and
remediating the one or more security vulnerabilities in the IoT device.
|