| CPC G06F 21/6245 (2013.01) [H04L 9/14 (2013.01); H04L 9/30 (2013.01); H04L 9/3247 (2013.01); H04L 9/50 (2022.05)] | 20 Claims |
|
1. A method comprising:
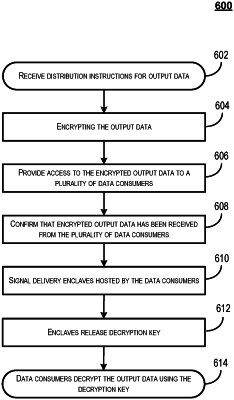
receiving distribution instructions for output data relating to a user of a client device, the distribution instructions comprising an indication of a plurality of data consumers;
encrypting the output data using a first cryptographic key;
providing access to the encrypted output data to each of the plurality of data consumers;
receiving, from each of the plurality of data consumers, an indication that the access to the encrypted output data was received by that data consumer; and
posting, a record comprising a plurality of indications that are respectively received from the plurality of data consumers and indicate that an access to the encrypted output data was received by the plurality of data consumers to a blockchain ledger respectively,
wherein, upon confirming with the blockchain ledger that the indication that each of the plurality of data consumers has been provided access to the encrypted output data, a second cryptographic key is provided to a plurality of private enclaves associated with computing devices operated by the plurality of data consumers, the second cryptographic key configured to be used by the data consumers to decrypt the encrypted output data.
|