| CPC G06F 21/55 (2013.01) [G06F 2221/033 (2013.01)] | 9 Claims |
|
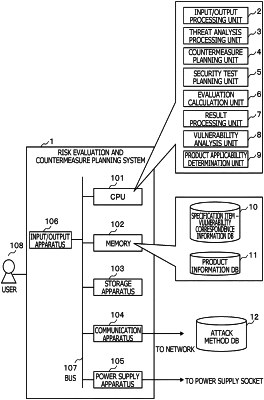
1. A risk evaluation and countermeasure planning system comprising:
a storage apparatus configured to store:
a vulnerability database that stores vulnerability information pertaining to a vulnerability, and
a product information database that stores product information; and
a processing apparatus including a memory and a processor coupled to the memory, the memory storing instructions that when executed by the processor, configures the processor to:
receive an input of design information,
analyze the vulnerability on a basis of the design information to generate an analysis result,
on a basis of the analysis result, analyze a threat to the system and output a threat analysis result,
on a basis of the output threat analysis result and the vulnerability information stored in the vulnerability database, plan a countermeasure plan which reduce an impact of the vulnerability,
plan a security test on a basis of the countermeasure plan,
perform an evaluation on a basis of the security test planned and output an evaluation result,
process the evaluation result, generate a security countermeasure as the product information, and store the security countermeasure as the product information database,
in a case where information regarding new vulnerabilities is input after product shipment, determine, from the information regarding new vulnerabilities and past product information, whether the information regarding new vulnerabilities applies to a product that forms a part of the system,
in a case that a result of the determination is that the information regarding new vulnerabilities applies to the product, evaluate an impact of the new vulnerabilities on the product, and determine whether an additional countermeasure is necessary by comparing the impact of the new vulnerabilities on the system with a requirement with respect to an asset value,
in a case where determination is that the additional countermeasure is necessary, plan the additional countermeasure for reducing the impact of the new vulnerabilities, and
generate the additional countermeasure as the product information, and store the product information in the product information database.
|