| CPC G06F 21/52 (2013.01) [G06F 21/40 (2013.01); G06F 2221/2113 (2013.01)] | 20 Claims |
|
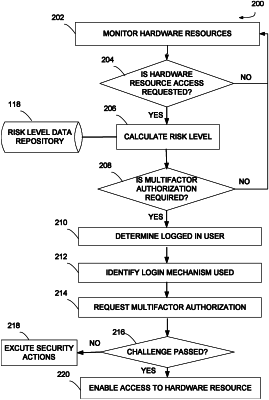
1. A computer-implemented method comprising:
receiving, by one or more processors, a request for a hardware resource from a plurality of hardware resources being monitored;
calculating, by one or more processors, a risk level of accessing the hardware resource of the request based on a respective risk level data repository, wherein the risk level in the respective risk level data repository indicates an action executed on the hardware resource when a risk level condition is met, the risk level condition being based on at least a device status associated with activity status of the hardware resource;
in response to a determination that the risk level requires multifactor authorization, determining, by one or more processors, that a user associated with the request is logged in;
identifying, by one or more processors, a mechanism used by the user to log in;
determining, by one or more processors, whether a challenge associated with the multifactor authorization based on the mechanism is successful; and
in response to a determination that the challenge associated with the multifactor authorization is successful, enabling, by one or more processors, access to the hardware resource of the request.
|