| CPC H04L 63/20 (2013.01) [H04L 63/029 (2013.01); H04L 63/0236 (2013.01); H04L 63/0263 (2013.01); H04L 63/1408 (2013.01); H04L 63/1433 (2013.01); H04W 12/48 (2021.01)] | 20 Claims |
|
1. A system, comprising:
a processor configured to:
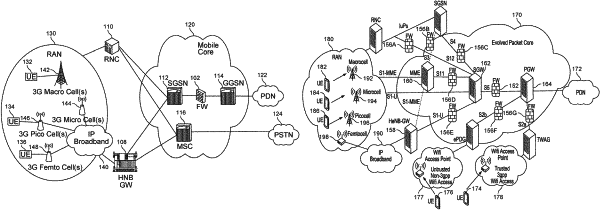
monitor network traffic on a service provider network at a security platform to identify a location, an application identifier, a signature, and a radio access technology (RAT) type for a new session, comprising to:
decrypt, using a cryptographic engine, the network traffic; traffic signature;
extract the location from a create session request message or a create PDP context request message from the network traffic, the location including three or more of the following: CGI (Cell Global Identifier), SAI (Service Area Identifier), RAI (Routing Area Identifier), TAI (Tracking Area Identifier), ECGI (E-UTRAN Cell Global Identifier), and LAC (Location Area Identifier);
determine the application identifier for user traffic associated with the new session at the security platform from the decrypted network traffic, comprising to:
monitor, via deep packet inspection, tunneled user traffic after the new session has been created to obtain the application identifier, wherein the application identifier relates to three of more of the following: web browsing using HyperText Transfer Protocol (HTTP), a Domain Name System (DNS) request, a file transfer using File Transfer Protocol (FTP), Telnet, Dynamic Host Configuration Protocol (DHCP), Transmission Control Protocol (TCP), User Datagram Protocol (UDP), or Trivial File Transfer Protocol (TFTP), and wherein the tunneled user traffic includes GPRS Tunneling Protocol User Plane (GTP-U) traffic;
determine that the decrypted signature of the network traffic matches a predefined signature; and
monitor GTP-C traffic in the decrypted network traffic to extract RAT information, comprising to:
extract the RAT type from a create session request message in the monitored GTP-C traffic, wherein the RAT type includes three or more of the following: UTRAN, GERAN, WLAN, GAN, HSPA, EUTRAN, Virtual, or EUTRAN-NB-IoT;
associate the location, the application identifier, the matched signature, and the RAT type with the new session at the security platform; and
determine a security policy to apply at the security platform to the new session based on the location, the application identifier, the matched signature, and the RAT type; and
a memory coupled to the processor and configured to provide the processor with instructions.
|