| CPC H04L 63/1441 (2013.01) [G06F 16/953 (2019.01); G06Q 20/085 (2013.01); H04L 63/1416 (2013.01); H04L 63/1433 (2013.01)] | 20 Claims |
|
1. A system, comprising:
a processor;
a network interface device; and
a non-transitory computer-readable medium having stored thereon instructions executable to cause the system to perform operations comprising:
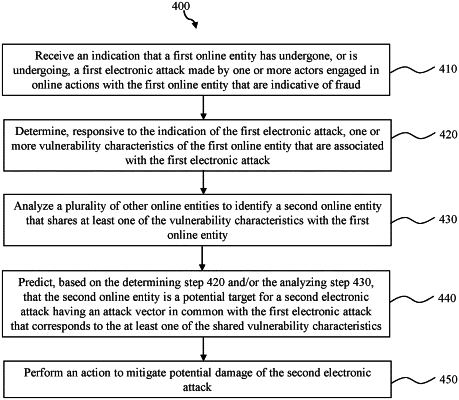
receiving an indication that a first set of computer systems corresponding to a first online entity has undergone or is undergoing a first electronic attack made by one or more actors engaged in one or more online actions with the first set of computer systems of the first online entity;
determining one or more vulnerability characteristics of the first set of computer systems corresponding to the first online entity that are associated with the first electronic attack;
analyzing a plurality of other computer systems corresponding to a plurality of other online entities to identify a second online entity that shares a set of at least one of the vulnerability characteristics with the first set of computer systems corresponding to the first online entity, wherein the analyzing comprises identifying the second online entity based on a determination that a first internet computing platform of the first online entity and a second internet computing platform of the second online entity both lack a particular protection mechanism, and wherein the first internet computing platform corresponds to the first set of computer systems and the second internet computing platform corresponds to the first set of computer systems, wherein the first online entity has control of a first set of one or more computing functions associated with the first internet computing platform but the second online entity does not have control of the first set of computing functions, and wherein the second online entity has control of a second set of one or more computing functions associated with the second internet computing platform but the first online entity does not have control of the second set of computing functions, wherein the first and second online entities are unrelated different entities;
determining, based on the shared set of vulnerability characteristics, that the second online entity is a potential target for a second electronic attack having an attack vector in common with the first electronic attack, wherein the attack vector corresponds to the set of shared vulnerability characteristics; and
performing an action to mitigate potential damage of the second electronic attack.
|