| CPC H04L 63/1416 (2013.01) [G06N 20/00 (2019.01); H04L 63/145 (2013.01); H04L 63/1425 (2013.01); G06N 7/01 (2023.01); G06N 20/20 (2019.01)] | 17 Claims |
|
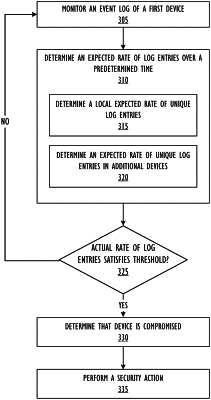
13. A method comprising:
processing, by executing an instructions with at least one processor, monitored log entries associated with a plurality of monitored devices to determine measurements associated with the monitored devices, the measurements including ones of a first type of entropy value and ones of a second type of entropy value associated respectively with the monitored devices, the ones of the first type of entropy value based on respective numbers of unique event identifiers included in respective groups of the monitored log entries associated respectively with the monitored devices, a first one of the second type of entropy value based on (i) a number of unique event identifiers included in a first one of the groups of the monitored log entries associated with a first one of the monitored devices and (ii) a total number of log entries included in the first one of the groups of the monitored log entries associated with the first one of the monitored devices;
determining, based on the measurements and a machine learning algorithm, whether the first one of the monitored devices is compromised; and
quarantining the first one of the monitored devices in response to a determination that the first one of the monitored devices is compromised.
|