| CPC H04L 63/1416 (2013.01) [G06F 21/566 (2013.01); H04L 63/0884 (2013.01); H04L 63/145 (2013.01); G06F 2221/2103 (2013.01); G06F 2221/2119 (2013.01); H04L 63/08 (2013.01); H04L 67/02 (2013.01)] | 19 Claims |
|
1. An apparatus, comprising:
a memory; and
a hardware processor communicatively coupled to the memory, the hardware processor configured to:
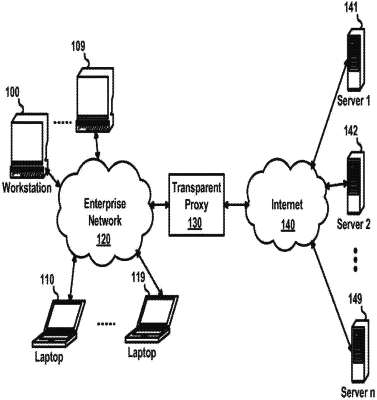
intercept a first communication from a first application executing at a first compute device, the first communication addressed to a first server;
intercept a second communication from a second application different from the first application and executing at a second compute device, the second communication addressed to a second server;
produce a first active content challenge for the first application based on the first communication, the hardware processor configured to send the first active content challenge to the first compute device;
produce a second active content challenge for the second application based on the second communication, the second active content challenge being different than the first active content challenge, the hardware processor configured to send the second active content challenge to the second compute device;
identify whether the first application is malicious based at least in part on whether the hardware processor receives a first automatic non-user-interactive application response from the first application within a first predetermined time period following sending the first active content challenge to the first compute device; and
identify whether the second application is malicious based at least in part on whether the hardware processor receives a second automatic non-user-interactive application response from the second application, different than the first automatic non-user-interactive application response, and within a second predetermined time period following sending the second active content challenge to the second compute device.
|