| CPC H04L 63/1416 (2013.01) [H04L 63/02 (2013.01); H04L 63/0428 (2013.01); H04L 63/1425 (2013.01); H04L 63/1441 (2013.01); H04L 63/20 (2013.01); H04L 63/166 (2013.01)] | 15 Claims |
|
1. A method, comprising:
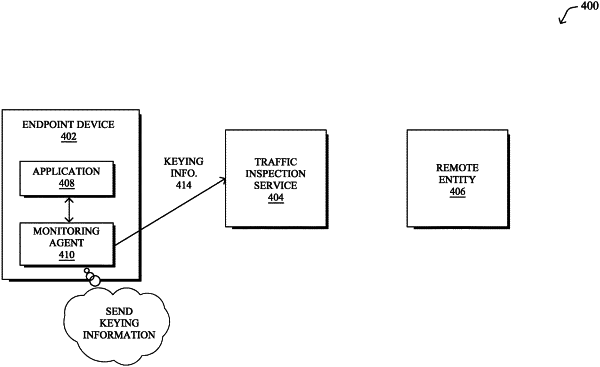
obtaining, by a traffic inspection service executed by an intermediary device and from a monitoring agent executed by an endpoint device, a keying information for an encrypted traffic session between the endpoint device and a remote entity, wherein the keying information a) comprises encryption keys exchanged between the endpoint device and the remote entity and b) is obtained, after the encrypted traffic session is formed, by the monitoring agent from a memory space of the endpoint device;
providing, by the traffic inspection service, a notification to the monitoring agent that acknowledges receipt of the keying information, wherein the monitoring agent delays transmission of packets via the encrypted traffic session by the endpoint device until the monitoring agent receives acknowledgement of the receipt of the keying information from the traffic inspection service;
using, by the traffic inspection service, the keying information to decrypt encrypted traffic from the encrypted traffic session, resulting in decrypted traffic;
applying, by the traffic inspection service and based on the decrypted traffic comprising a file from the encrypted traffic session suspected of containing protected information, a policy to the encrypted traffic session between the endpoint device and the remote entity to determine whether the decrypted traffic is against a privacy policy; and
performing, by the traffic inspection service, a mitigation action in response to a determination that the decrypted traffic is against the privacy policy.
|