| CPC H04L 63/0236 (2013.01) [H04L 45/38 (2013.01); H04L 47/2483 (2013.01); H04L 63/0227 (2013.01); H04L 63/1408 (2013.01); H04L 45/64 (2013.01)] | 20 Claims |
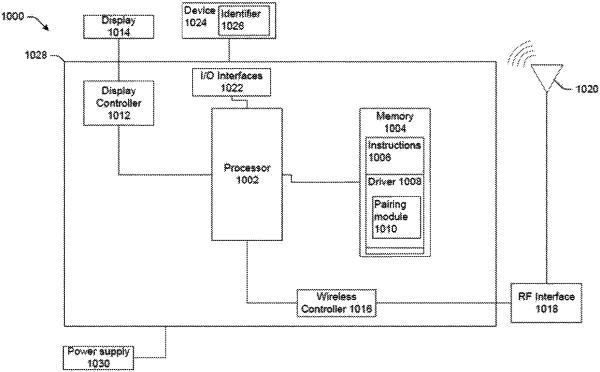
|
1. A network controller comprising:
memory including computer readable instructions; and
processor circuitry to execute the computer readable instructions to at least:
assign role tags to a plurality of network devices in a data flow path corresponding to a data flow path identifier, the role tags to specify respective roles of respective ones of the plurality of network devices, the role tags including at least a source role tag to specify a source role and a destination role tag to specify a destination role, the source role tag to be assigned to a first group of one or more of the network devices via which data enters the data flow path, and the destination role tag to be assigned to a second group of one or more of the network devices via which data exits the data flow path;
when activity classified as malicious is detected on the data flow path, identify, based on the data flow path identifier and the role tags, the first group of the network devices assigned the source role; and
cause a blocking flow rule to be transmitted to the first group of the network devices, the first group of the network devices to respond to the blocking flow rule by blocking data from entry to the data flow path.
|