| CPC G06Q 40/04 (2013.01) [G06Q 20/0655 (2013.01); G06Q 20/3825 (2013.01); G06Q 20/3829 (2013.01); G06Q 20/401 (2013.01); H04L 9/14 (2013.01); H04L 9/3073 (2013.01); H04L 9/3247 (2013.01); G06Q 2220/00 (2013.01); H04L 2209/46 (2013.01); H04L 2209/56 (2013.01)] | 20 Claims |
|
1. A method for safe creation, custody, recovery and management of a digital asset, agnostic to an underlying blockchain technology, the method comprising:
a preliminary phase, the preliminary phase comprising:
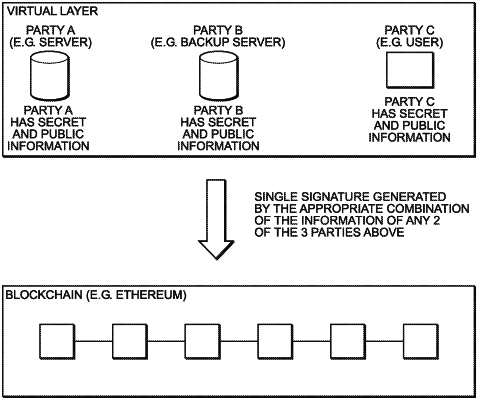
establishing a virtual layer;
establishing, by a backup server, a non-ephemeral private-public information pair in the virtual layer; and
sending public information of the non-ephemeral private-public information pair to a service provider server;
an enrollment phase in which the backup server is offline, the enrollment phase comprising:
receiving an enrollment request from a user server at the service provider server;
sending the public information of the non-ephemeral private-public information pair from the service provider server to the user server; and
generating, in the virtual layer:
a first data shard pair comprising a provider-backup shard and a provider-user shard, the first data shard pair corresponding to secret information of the service provider server;
a second data shard pair comprising a user-provider shard and a user-backup shard, the second data shard pair corresponding to secret information of the user server;
a backup-provider shard generated on the service provider server;
a backup-user shard generated on the user server;
a first private key controlled by the service provider server, the first private key computed from the backup-provider shard and the user-provider shard; and
a second private key controlled by the user server, the second private key computed from the backup-user shard and the provider-user shard;
an ordinary signature phase in which the backup server is offline, the ordinary signature phase comprising:
transacting the digital asset by using the first private key and the second private key and multi-party computation techniques, with no single entity and device directly controlling the digital asset; and
a recovery signature phase, wherein the first private key or the private second key becomes unavailable, the recovery signature phase comprising:
bringing the backup server online;
sending the backup-provider shard and the backup-user shard to the backup server;
generating, in the virtual layer, a third private key controlled by the backup server, the third private key computed from the backup-provider shard, the backup-user shard, and the private information from the non-ephemeral private-public information pair; and
recovering the digital asset using either a combination of the first private key and the third private key or of the second private key and the third private key.
|