| CPC G06Q 20/3829 (2013.01) [G06Q 20/204 (2013.01); G06Q 20/3821 (2013.01); G06Q 20/385 (2013.01); G06Q 20/4014 (2013.01); H04L 9/0819 (2013.01); H04L 9/0861 (2013.01); H04L 9/14 (2013.01); H04L 63/0428 (2013.01); H04L 63/067 (2013.01); H04L 63/08 (2013.01); H04W 12/033 (2021.01); H04W 12/10 (2013.01); G06Q 20/321 (2020.05); G06Q 2220/00 (2013.01); H04L 63/126 (2013.01); H04L 2209/56 (2013.01); H04L 2463/062 (2013.01); H04W 12/04 (2013.01)] | 10 Claims |
|
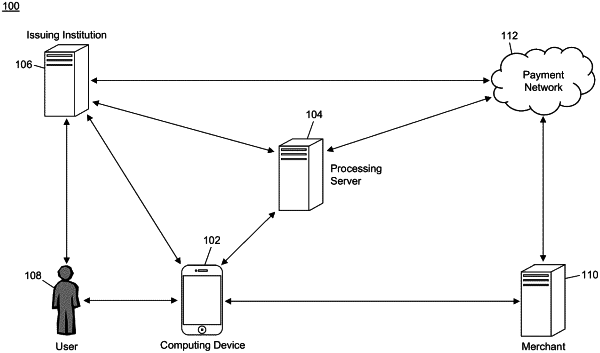
1. A method for provisioning of a session key for use in generating an application cryptogram for use in a payment transaction, said method comprising:
storing, in an account database of a processing server, an account profile, wherein the account profile includes at least an account identifier and an account identification number;
receiving, by a receiving device of the processing server, from a computing device, a session key request including a single use key and the account identifier, wherein the single use key is a payment token that is specifically associated with a transaction account;
receiving, by the receiving device of the processing server, from the computing device, a result of an integrity evaluation, performed by the computing device, of each of a plurality of memories of the computing device configured to store single use keys, encrypted session keys, and server encryption keys;
generating, by a generation module of the processing server, a session key based on at least the received single use key and the account identification number included in the account profile;
encrypting, by an encryption module of the processing server, the generated session key using a server encryption key; and
electronically transmitting, by a transmitting device of the processing server, at least the encrypted session key and the server encryption key to the computing device where the application cryptogram is generated without requiring input of a personal identification number (PIN).
|