| CPC G06F 8/65 (2013.01) [G06F 8/71 (2013.01); H04L 67/34 (2013.01)] | 1 Claim |
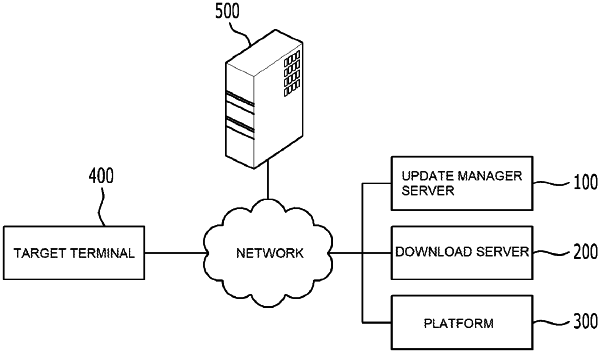
|
1. A firmware updating method using a low-power wireless network, comprising:
receiving and registering information of a target terminal on which the firmware is updated in an update manager server from a manufacturer server, wherein receiving and registering includes:
receiving and registering, by the update manager server, manufacturer information of the target terminal and information of vehicle terminal on which the target terminal is installed from the manufacturer server;
storing the manufacturer information and the vehicle terminal information registered by the update manager server in a database;
receiving and registering, by a platform, the manufacturer information and the vehicle terminal information from the update manager server;
receiving, by the update manager server, a token which is a unique ID corresponding to the vehicle terminal information from the platform; and
transmitting the token received from the update manager server to the manufacturer server;
receiving, by the target terminal, the token from the manufacturer server,
checking information of a firmware version on the target terminal using the low-power wireless network in the platform managing an update firmware on the target terminal, wherein the checking of the firmware version includes:
the checking of the firmware version includes:
periodically transmitting, by the target terminal, the information of the firmware version to the platform; and
checking, by the update manager server, the information of the firmware version on the target terminal transmitted to the platform;
receiving the update firmware from the manufacturer server in a download server and packaging the received update firmware to the target terminal, wherein packaging the received update firmware includes:
receiving, by the download server, the firmware from the manufacturer server;
packaging the firmware received by the download server to create a firmware for transmission to which division and security are applied;
storing the firmware for transmission created by the download server in the database;
uploading a firmware download directory (URL) of the firmware for transmission created by the download server to the update manager server;
creating, by the update manager server, a firmware update notice;
transmitting, by the update manager server, the created firmware update notice to the platform;
transmitting a firmware update notification received by the platform to the target terminal; and
transmitting, by the update manager server, a transmission result of the firmware update notice to the manufacturer server;
downloading the packaged firmware from the download server in the target terminal through the low-power wireless network, wherein downloading includes:
downloading, by the target terminal, the firmware for transmission from the download server, wherein downloading the firmware includes:
automatically performing a firmware download at a specific time and when vehicle driving is finished wherein the automatically performing adjusts the downloading when the firmware download has failed three or more times;
while performing the firmware download, detecting an intrusion from outside of the network;
in response to the detecting the intrusion, duplicating primary and secondary backup files to create a plurality of sub-backup files of the firmware; and
individually storing the created plurality of sub-backup files in different locations created according to random variables;
transmitting, by the target terminal, the download result to the platform;
checking, by the update manager server, the download result through the platform;
and
transmitting, by the update manager server, the download result to the manufacturer server; and
performing the firmware update by unpackaging the firmware packaged in the target terminal, the updating of the firmware includes:
preparing the firmware update by unpackaging the firmware for reception received by the target terminal;
performing, by the target terminal, the firmware update when the preparation of the update is completed;
transmitting, by the target terminal, the result of the firmware update to the platform;
checking, by the update manager server, the result of the firmware update through the platform; and
transmitting, by the update manager server, the result of the firmware update to the manufacturer server,
wherein
the packaging the firmware received by the download server to create the firmware for transmission to which division and security are applied comprises:
dividing, by the download server, a firmware input from the manufacturer server into a plurality of blocks, which include a first block including a firmware name and a firmware version, a plurality of firmware blocks that are arranged in order after the first block and are each allocated part of firmware data to form one firmware data as a whole, and a last block arranged after the last firmware block to notify a termination of the packaging; and
separately encrypting, by the download server, each block of the divided plurality of blocks of the firmware input, wherein the separately encrypting comprises:
encrypting the first block, which includes:
“Info” including the firmware name and the firmware version as a header; and
“Sign(H(Info))” that is data of hashing the information included the “info” and then signing on the hashed value of the information included the “info” as a body;
encrypting each block of the plurality of firmware blocks, which includes:
“Firmware” including the firmware name, an output value when firmware data is used as an input of a hash function, and a sign value obtained by substituting, as an input, the output value when the firmware data is used as the input of the hash function as a header;
“H(FW)” that is data of hashing the information included the “Firmware” as a body;
“Sign(H(FW)) that is data of signing on the hashed value of the “H(FW)” as another body; and
encrypting the last block, which includes:
“H(F/W)” that is data of hashing the firmware data as a header;
“Sign(H(F/W)) that is data of signing on the hashed value of the “H(F/W)” as a body,
wherein the preparing the firmware update by unpackaging the firmware for reception received by the target terminal comprises:
a version checking step of reading whether the firmware update of the target terminal is necessary through an info value included in the first block after a target terminal communicating with the download server decodes the first block and comparing the info value whose sign and hash are released and an info value previously included in the first block when the firmware update is necessary; and
a data merging step of comparing the hash value of the firmware data whose sign is released and the hash value of the firmware data previously included in the firmware block after the target terminal downloads and decodes the firmware blocks when the version is checked in the version checking step, and merging each of the firmware data divided when the hash value of the firmware data whose sign is released is equal to the hash value of the firmware data previously included in the firmware block, and
wherein the performing the firmware update comprises: when the decoding of the last block is completed, the firmware update is performed using the merged firmware data.
|