| CPC G06F 21/6254 (2013.01) [G06F 21/33 (2013.01); H04L 9/0866 (2013.01); H04L 9/3213 (2013.01); H04L 2209/56 (2013.01)] | 20 Claims |
|
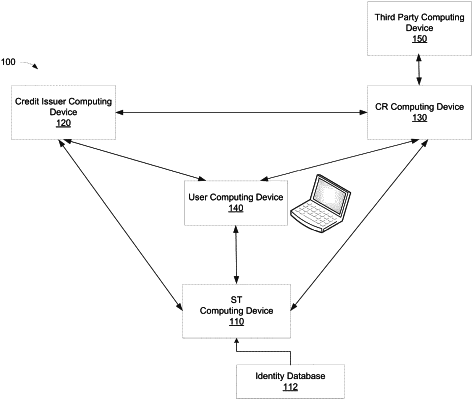
1. A secure token (ST) system for provisioning data using secure tokens over a network, wherein the ST system comprises a ST computing device including at least one processor in communication with a database, and wherein the at least one processor is configured to:
receive first user data from a third party computing device, via network communication in a secure processing domain, the first user data including one or more data record identifiers associated with a stored data record of a user and a user identifier for identifying the user;
generate a hash value for the first user data using the one or more data record identifiers and the user identifier;
generate a secure token by combining the hash value and one or more unique identifiers associated with the one or more data record identifiers of the user, wherein the secure token identifies a user profile associated with the user;
transmit the secure token, via network communication in the secure processing domain, to at least one of the third party computing device or an additional third party computing device;
receive, from at least one requesting party computing device via network communication in the secure processing domain, a user data request associated with the one or more data record identifiers, wherein the user data request includes the secure token, wherein the at least one requesting party computing device is at least one of the third party computing device or the additional third party computing device, and wherein the at least one requesting party computing device is not required to store the user identifier, thereby reducing vulnerability of the at least one requesting party computing device to data breaches involving the user identifier; and
in response to the user data request, transmit, via network communication in the secure processing domain, second user data of the user to the at least one requesting party computing device.
|