| CPC G06F 21/6209 (2013.01) [G06F 16/24566 (2019.01); G06F 16/9017 (2019.01)] | 20 Claims |
|
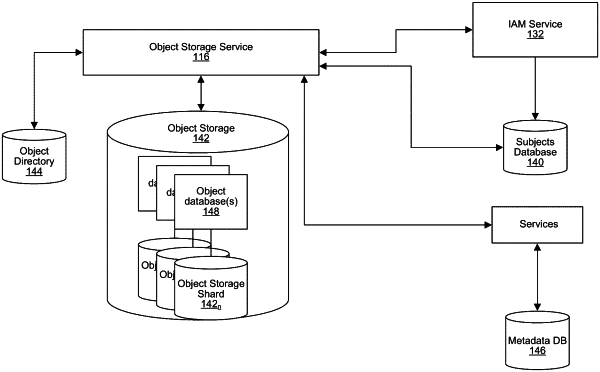
1. A method to determine if a user account can access data pertaining to an object ID, the method comprising:
determining a list of ancestors of the object ID;
obtaining a permission statement for each ancestor in the list of ancestors and the object ID;
ordering the obtained permission statements into an ordered list according to inheritance properties of the respective permission statements; and
iterating through the ordered list of the obtained permission statements, in order, until one of the obtained permission statements in the ordered list grants or denies access to the object.
|