| CPC G06F 21/604 (2013.01) [G06F 21/566 (2013.01); G06F 21/602 (2013.01); G06F 2221/034 (2013.01); G06F 2221/2113 (2013.01)] | 17 Claims |
|
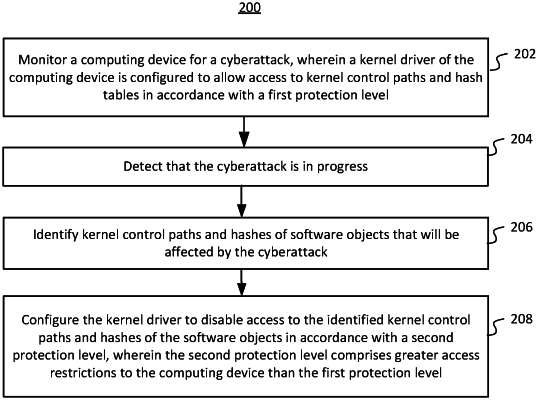
1. A method for adjusting data protection levels based on system metadata, the method comprising:
monitoring a computing device for a cyberattack, wherein a kernel driver of the computing device is configured to allow access to kernel control paths and hash tables in accordance with a first protection level;
detecting that the cyberattack is in progress;
while the cyberattack is in progress,
identifying kernel control paths and hashes of software objects that will be affected by the cyberattack;
configuring the kernel driver to disable access to the identified kernel control paths and hashes of the software objects in accordance with a second protection level, wherein the second protection level comprises greater access restrictions to the computing device than the first protection level.
|