| CPC H04L 9/3213 (2013.01) [H04L 9/30 (2013.01); H04L 9/3247 (2013.01); H04L 63/0457 (2013.01)] | 19 Claims |
|
1. A computer-implemented method for secure stream distribution, the computer-implemented method comprising:
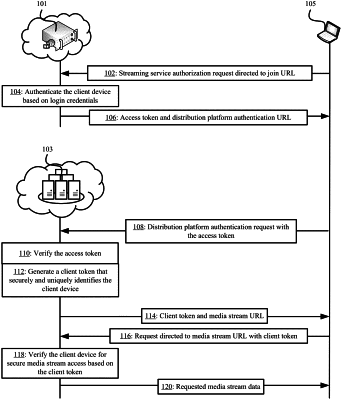
receiving a first request from a client device at a first network node, wherein the first request comprises a first link for a particular stream of a streaming service that is accessed from a first domain associated with the first network node;
performing a first verification of the client device at the first network node based on one or more credentials provided by the client device matching stored credentials for the client device at the first network node;
generating a first token in response to performing the first verification, wherein generating the first token comprises encoding unique identifying information of the client device and a signature as part of the first token;
providing the first token with a second link to the client device in response to the first request and performing the first verification, wherein the second link is directed to a second domain associated with a second network node that distributes the particular stream on behalf of the streaming service;
determining, at the second network node, that the first network node performed the first verification of the client device based on a second request from the client device that includes the first token and that is directed to the second domain;
generating, at the second network node, a second token in response to determining that the first network node performed the first verification, wherein generating the second token comprises encoding a link to specific data of the particular stream and two or more identifiers that uniquely identify the client device in the second request; and
streaming the specific data from the second network node to the client device in response to performing a second verification of the client device at the second network node based on one or more requests for the specific data comprising the second token and the two or more identifiers encoded as part of the second token.
|