| CPC H04L 67/34 (2013.01) [H04L 67/01 (2022.05); H04L 67/125 (2013.01); H04L 67/51 (2022.05)] | 20 Claims |
|
1. A computer-implemented method for validating deployment of a service, the method comprising:
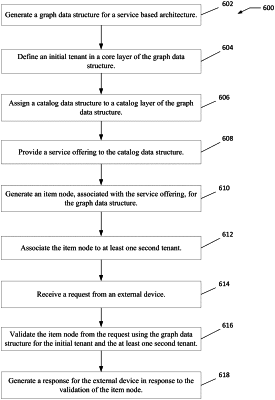
assigning a catalog data structure to a catalog layer of a plurality of layers of a graph data structure, the catalog data structure including data associated with an initial tenant at an address associated with a hosted location;
providing a service offering to the catalog data structure of the catalog layer;
generating an item node, associated with the service offering, for the graph data structure, wherein the graph data structure associates the item node to the catalog data structure of the catalog layer and the initial tenant; and
validating, through a static analysis of the graph data structure, the item node with respect to a build that exposes the service offering;
determining, via the static analysis, that the build that exposes the service offering deviates from a pre-declared listing of allowed of one or more dependencies; and
rejecting, responsive to the determination, the deployment of the service after the deployment is inserted into the graph data structure to enforce, at least in part, a default security policy to deny deviations from pre-declared execution parameters.
|