| CPC H04L 63/205 (2013.01) [H04L 9/40 (2022.05); H04L 63/0209 (2013.01); H04L 63/101 (2013.01)] | 8 Claims |
|
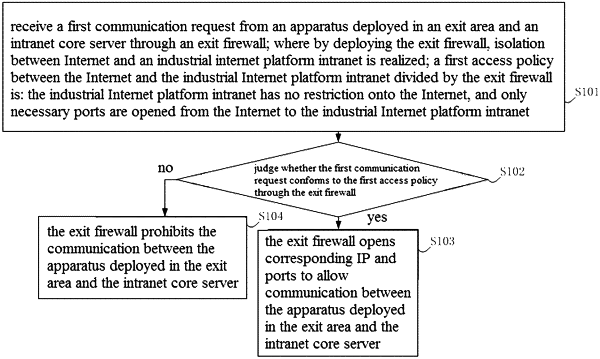
1. A security protection method based on industrial Internet, comprising:
receiving a first communication request from an apparatus deployed in an exit area and an intranet core server through an exit firewall; wherein by deploying the exit firewall, isolation between Internet and an industrial internet platform intranet is realized; a first access policy between the Internet and the industrial Internet platform intranet divided by the exit firewall is: the industrial Internet platform intranet has no restriction onto the Internet, and only necessary ports are opened from the Internet to the industrial Internet platform intranet;
judging whether the first communication request conforms to the first access policy through the exit firewall;
wherein if the first communication request conforms to the first access policy, the exit firewall opens corresponding Internet Protocol and ports to allow communication between the apparatus deployed in the exit area and the intranet core server;
if the first communication request fails to conform to the first access policy, the exit firewall fails to open corresponding Internet Protocol and ports to allow the communication between the apparatus deployed in the exit area and the intranet core server;
receiving a second communication request from secondary nodes of the industrial Internet platform intranet and the intranet core server through a regional firewall; wherein by deploying the regional firewall, isolation between the intranet core server and each of the secondary nodes is realized; the regional firewall is deployed on a wide area network router, and a second access policy of the secondary nodes and the intranet core server is preset, after formulation of the second access policy is completed only Internet Protocol and service ports of a specific host are opened, and all other accesses are prohibited;
judging whether the second communication request conforms to the second access policy through the regional firewall;
wherein if the second communication request conforms to the second access policy, the regional firewall opens the Internet Protocol and the service ports of the specific host to allow communication between the secondary nodes and the intranet core server;
if the second communication request fails to conform the second access policy, the regional firewall fails to open the Internet Protocol and the service ports of the specific host to allow the communication between the secondary nodes and the intranet core server;
wherein the method further comprises:
realizing storage access isolation between virtual machines through a virtualization layer, isolating user data;
performing authority control between a user and a virtual machine image, performing authority confirmation on mounted volume of the user, and performing access control on an object storage user object;
performing complete data erasure before storage resources being redistributed to Virtual Machine, and after stored user files/objects are deleted, performing complete data erasure on a corresponding storage area or marking as write-only;
wherein data storage and backup adopt following policies: defining a database data storage path to a special disk array storage medium; performing data backup in a manner of combining full backup and differential backup; performing the full backup once a week and performing the differential backup of business data once a day; saving and managing backup data in different places;
responsibly simulating all physical apparatuses of the virtual machines through a virtual machine monitor and physically isolating virtual machine apparatus; supporting to isolate between the virtual machines by dividing VLAN, and supporting virtual machine security group; for protection of a malicious virtual machine, realizing a function of preventing address spoofing, restricting the virtual machines to only send message with local addresses, supporting detection of Virtual Machine port scanning and sniffing behavior, blocking memory and storing allocation policies, and emptying contents of a memory page when allocating memory for the virtual machines and other user-mode processes; emptying contents of all disk image files when deleting the virtual machines; when storage space is newly allocated for the virtual machines, emptying contents in a corresponding disk block; preventing data of the virtual machines from being accessed at will, using a mandatory access control security policy; in a physical machine, accessing virtual machine resources only by a specific virtualization management program, and not capable of accessing the virtual machine resources by all other programs no matter running under any identity; encrypting and storing disk data of the virtual machines in the physical machine; preventing network monitoring and address spoofing, binding Mac address and IP Internet Protocol address of the virtual machines in the physical machine, and not capable of modifying itself Internet Protocol address and Mac address by the virtual machines, respectively establishing a management communication network card of the physical machines and a virtual machine share network card, and completely shielding the virtual machines from a network card used by the physical machine itself; in the physical machine, providing a perfect network access rule firewall for all running virtual machines, effectively discovering and preventing illegal access attempts initiated by the virtual machines; wherein network security realization among the virtual machines in virtualized network depends on virtual security module function; wherein a virtual security function module comprises a virtual module security agent function, a virtual module manager function and a virtualized security management center; wherein a virtualized security agent module is deployed on a protected server or virtual machines; a virtualization security manager module provides centralized policy management, issues security updates and monitors through alarms and reports; a virtualization security manager center is a hosted portal and develops rule updates for newly emerging threats through the portal, and then a security manager issues these updates regularly; servers in application system domain are deployed in a same security domain, and corresponding application services are deployed on the physical machine and the virtual machines; according to security protection specification of hierarchical protection, further logical isolating and access controlling are performed on different application services in the same security domain.
|