| CPC H04L 63/1441 (2013.01) [G06F 16/90344 (2019.01); G06N 20/00 (2019.01); H04L 51/08 (2013.01); H04L 51/212 (2022.05); H04L 63/1433 (2013.01)] | 15 Claims |
|
1. A method comprising:
receiving, via a communication interface of an enterprise computing platform, a plurality of electronic messages;
identifying, by an information security platform, an incoming message comprising executable code for execution by a processor of computing device addressed as a recipient of the message;
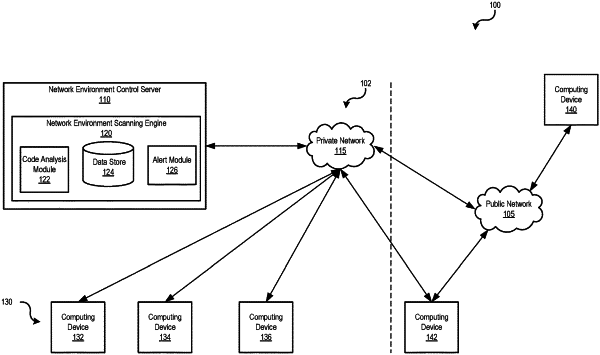
identifying, by a machine-learning based algorithm, whether the executable code comprises instructions targeting a known vulnerability of an operating system of the computing device identified as the recipient of the message;
analyzing, using the machine-learning based algorithm in a virtual security environment, the executable code to identify whether the executable code comprises one or more environment variables that match a format unique to an enterprise computing environment comprising an enterprise computing network, wherein the virtual security environment is configured to resemble the enterprise computing environment by including enterprise-specific environment variables and wherein the format unique to the enterprise computing environment comprises one or both of customized environment variables and formatting rules customized and unique to the enterprise computing environment, wherein the customized environment variables and formatting rules unique to the enterprise computing environment are unknown outside the enterprise computing environment;
identifying, based on inclusion of customized environment variables that are unique to the enterprise computing network, an attempt to bypass external controls by using environment variables unknown outside the enterprise computing environment; and
triggering, based on identification of one or more environment variables that match the format unique to the enterprise computing network within the executable code and by an electronic messaging system, an alert sent via a communication network identifying suspect use of the one or more environment variables and identifying an intrusion attempt to bypass security measures of the enterprise computing network.
|