| CPC H04L 63/1425 (2013.01) [H04L 63/1458 (2013.01); H04L 61/4511 (2022.05)] | 16 Claims |
|
1. A method, comprising:
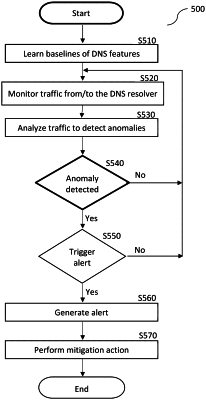
learning a plurality of baselines of at least rates and rate invariants of domain name system (DNS) features;
monitoring DNS traffic directed to and from a DNS resolver, wherein the DNS resolver is communicatively connected between at least one client and at least one name server;
analyzing the monitored DNS traffic using at least one detection function to detect in the monitored DNS traffic at least one anomaly based on at least one baseline of the plurality of learnt baselines, each of the at least one anomaly indicating a potential attack upon a domain name;
determining, based on the detected at least one anomaly, that a recursive DNS attack upon the domain name is in progress; and
upon detection that the recursive DNS attack upon the domain name is in progress, performing at least one mitigation action to filter out incoming DNS queries to the domain name is under attack, wherein performing the mitigation action determines which domain name is the domain name under attack;
wherein the least one detection function is a fuzzy logic function set based on the at least one baseline of the plurality of learnt baselines.
|