| CPC H04L 63/1416 (2013.01) [G06F 17/18 (2013.01); G06F 21/566 (2013.01); G06N 20/00 (2019.01); H04L 43/022 (2013.01); H04L 43/16 (2013.01); H04L 63/1466 (2013.01); H04L 69/322 (2013.01)] | 19 Claims |
|
1. A system for detecting malicious traffic in a network comprising:
at least one sensor, wherein each sensor is configured to:
mirror network traffic for at least one device connected to the network; and
create a set of data consisting of transfer protocol records and associated transfer protocol record metadata by, over a time interval, parsing the mirrored network traffic for transfer protocol records;
a database coupled to the at least one sensor and configured to:
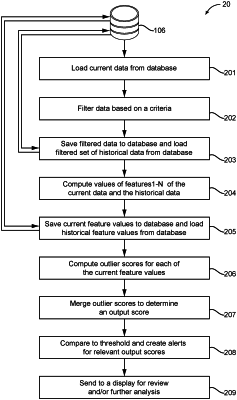
receive and store the set of data from each of the at least one sensor, wherein the data received and stored during the time interval comprise a set of test data;
store a set of historical data previously obtained from the network, wherein the historical data consists of transfer protocol records and associated transfer protocol metadata; and
a computation engine including at least one processor and non-transitory memory, the computation engine including a detection module configured to run on the computation engine and adapted and configured to perform the steps of:
loading the set of test data from the database;
filtering the set of test data to obtain filtered data based on at least one criterion,
wherein the filtered data includes data for at least one transfer protocol record;
saving the filtered data to the database;
determining a value of each of a plurality of features of each transfer protocol record;
loading, for each transfer protocol record, a set of previously computed historical feature values from the database, wherein the historical feature values were computed from the set of historical data; and
computing an output score for each transfer protocol record based on comparing, for each feature of each transfer protocol record, the determined value to the set of previously computed historical feature values for that feature, wherein the output score for each transfer protocol record indicates the likelihood that that transfer protocol record represents malicious network traffic.
|