| CPC H04L 63/10 (2013.01) [G06F 9/44526 (2013.01); G06F 21/41 (2013.01); G06F 21/45 (2013.01); H04L 63/08 (2013.01); H04L 63/0815 (2013.01); G06F 21/64 (2013.01)] | 19 Claims |
|
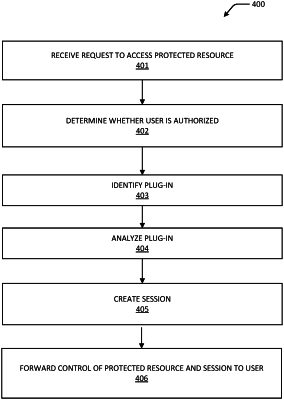
1. A method performed by a computing system of a cloud computing environment for injecting user pre-authentication and post authentication configurations, the method comprising:
receiving a request from a user of the cloud computing environment to access a protected resource managed by the computing system, wherein the protected resource comprises an application;
determining via an identity service authentication process whether the user is a tenant of the cloud computing environment that is authorized to access the protected resource with a plug-in;
in response to determining that the user is authorized to access the protected resource, identifying one or more pre-authentication or post authentication plug-ins configured by the user for controlling an authentication session for the protected resource,
wherein a plug-in is configured by the user to control a user session in a browser,
wherein a type of the plug-in that is configured by the user varies depending on a role of the user configuring the plug-in, and wherein the plug-in is configured to include a public key of the user;
analyzing the one or more plug-ins generated by the user to determine whether the one or more plug-ins can be implemented for a session, wherein the one or more plug-ins can be implemented for the session based on criteria ensuring correct operation of the one or more plug-ins in the computing system are satisfied, wherein the criteria comprises mandatory criteria that is required for the plug-in to be initiated or optional criteria that is optional before the plug-in initiated, wherein the one or more plug-ins are generated by the user prior to the request to access the protected resource;
in response to verifying that the criteria for implementing the one or more plug-ins customized by the user are satisfied, creating a session for the user; and
forwarding control of the protected resource and the session to the user.
|