| CPC H04L 63/0272 (2013.01) [G06F 9/547 (2013.01); H04L 9/006 (2013.01); H04L 9/0894 (2013.01); H04L 9/14 (2013.01); H04L 9/30 (2013.01); H04L 9/3263 (2013.01); H04L 63/029 (2013.01); H04L 63/0823 (2013.01); H04L 63/0876 (2013.01); H04L 67/01 (2022.05); H04L 67/1021 (2013.01); H04L 61/4511 (2022.05); H04L 61/59 (2022.05)] | 17 Claims |
|
1. A method comprising:
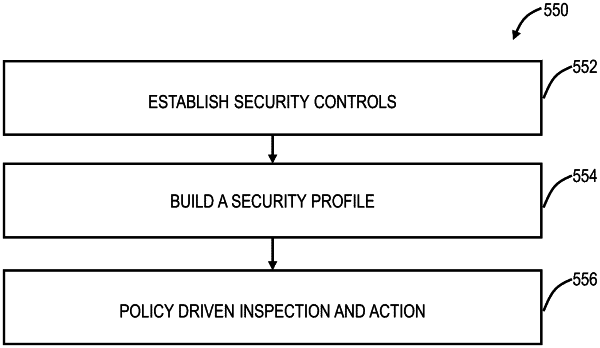
responsive to determining a user can access an application via a cloud-based system, wherein the application is in one of a public cloud, a private cloud, and an enterprise network, and wherein the user is remote over the Internet, obtaining a predetermined inspection profile for the user with the inspection profile including a plurality of rules evaluated in an order, wherein obtaining the predetermined inspection profile is based on the application and the user;
storing the plurality of rules in rows of database as strings;
responsive to the obtaining, obtaining a copy of a template file and filtering the template file based on a mapping table, wherein the template file comprises dependency information for the plurality of rules and a set of tags for each rule, and wherein the mapping table comprises rule definitions and rule inclusions and exclusions;
replacing the tags with rule data from the database;
performing inspection of transactions between a user device associated with the user and the application during the access, the inspection being performed based on the plurality of rules, each rule having dependencies maintained with other rules, in the predetermined inspection profile, wherein the rules are investigated in an order based on the dependencies; and
responsive to results of any of the plurality of rules, one or more of monitoring, allowing, blocking, and redirecting the access, via the cloud-based system.
|