| CPC H04L 51/212 (2022.05) [H04L 51/42 (2022.05); H04L 63/1433 (2013.01); G06N 20/00 (2019.01)] | 20 Claims |
|
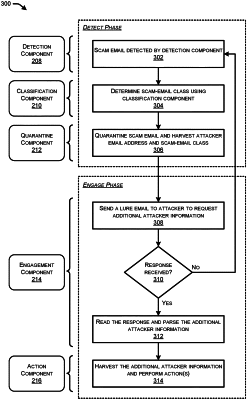
1. A method for an email-security system to detect scam emails, the method comprising:
obtaining, at the email-security system, a first email sent from a sending email address and to a targeted email address;
determining, at the email-security system, that the first email is a scam email that is a scam directed at a targeted user associated with the targeted email address;
classifying the scam email into a particular scam-email class from amongst a group of scam-email classes;
determining, based at least in part on the particular scam-email class, additional information that is unique to a sending user associated with the sending email address in order to complete the scam;
determining a response that prompts the sending user for the additional information needed to perform the scam;
sending, to the sending email address, a second email that includes the response that prompts the sending user for the additional information associated with the scam;
receiving, from the sending email address, a third email that includes the additional information associated with the scam;
harvesting the additional information from a body of the third email;
generating a rule to block subsequent emails based on bodies of the subsequent emails including the additional information that is unique to the sending user;
identifying the additional information in a second body of a subsequent email sent to a second targeted email address; and
based at least in part on the rule, preventing the subsequent email from being sent to a second inbox of the second targeted email address.
|