| CPC G06Q 10/103 (2013.01) [G06F 9/452 (2018.02); H04L 63/08 (2013.01)] | 20 Claims |
|
1. A computer-implemented method for cloud desktop-as-a-service administration, the method comprising:
receiving, at a server, workspace-type selection data from a first user logged into the server on a first user device;
receiving, at the server, workspace configuration selection data from the first user; generating, on the server, a remote desktop workspace, wherein
the remote desktop workspace includes a number of remote desktop sessions, the number is based on the workspace-type selection data, and
each remote desktop session includes a virtualized hardware configuration based on the workspace configuration selection data;
receiving, at the server, user data from a second user device, wherein the user data includes a request for a second user to join a remote desktop session of the remote desktop workspace;
permitting the second user to join the remote desktop session;
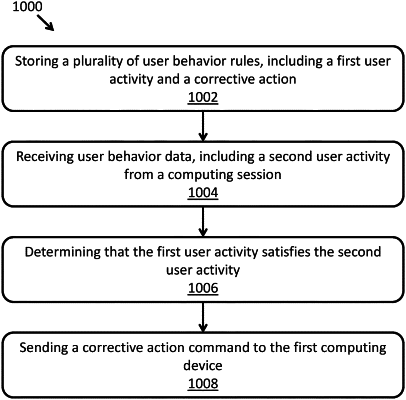
determining whether a first detected user action performed by at least one of the first and second users satisfies a trigger condition of a user behavior rule of a plurality of user behavior rules; and either,
based at least in part on a determination that the first detected user action performed by at least one of the first and second users satisfies the trigger condition of the user behavior rule:
performing a corrective action specified by the user behavior rule and associated with the first detected user action, wherein the action performed comprises blocking completion of the first detected user action; or
based on a user input:
generating at least one new user behavior rule comprising at least one new trigger condition comprising the first detected user action and a new corrective action configured to block completion of the first detected user action in one or more subsequent computing sessions based at least in part on a determination that the at least one new trigger condition is satisfied in one or more of the subsequent computing sessions.
|