| CPC G06F 9/44589 (2013.01) [G06F 9/44505 (2013.01); G06F 9/44578 (2013.01); G06F 11/3457 (2013.01)] | 15 Claims |
|
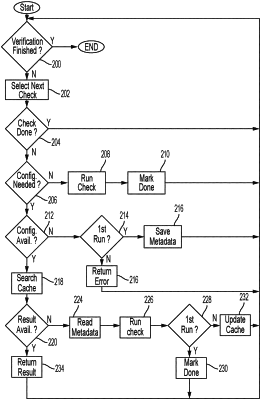
1. A method for checking program code having a program instruction, the method comprising:
in response to a first command from a host computing device in communication with a computational storage device of a computing system to load the program code, executing by the host computing device a first check of the program code loaded into the computing system for execution, wherein the first check includes making a determination about availability of memory configuration data for the program instruction, wherein the memory configuration data is for configuring a memory for executing the program code;
identifying, based on the determination about the availability of the memory configuration data, metadata for accessing the memory by the program instruction; and
storing the metadata in a first data structure in the memory;
in response to a program execute command from the host computing device to execute the program code, running, by the computational storage device in an execution mode of the program code, a second check of the program code, wherein the running of the second check includes:
identifying the memory configuration data in the memory;
retrieving the metadata by accessing the memory from the first data structure;
determining validity of access to the memory by the program instruction based on the memory configuration data and the metadata;
building a second data structure in the memory; and
storing a result of the second check in the second data structure in the memory; and
executing by the computing system the program code based on the stored result of the second check determining the validity of access to the memory.
|