| CPC G06F 21/6218 (2013.01) [G06F 21/554 (2013.01); G06F 2221/031 (2013.01)] | 14 Claims |
|
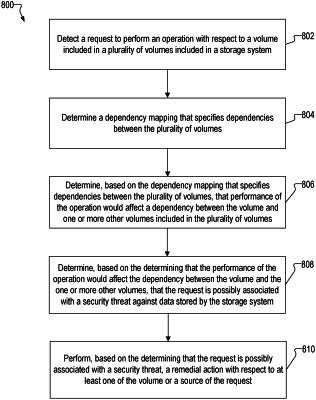
1. A method comprising:
detecting, by one or more computer processors, a request to perform an operation with respect to a volume included in a plurality of volumes included in a storage system;
determining, by the one or more computer processors based on a dependency mapping that specifies dependencies between the plurality of volumes, that performance of the operation would affect a dependency between the volume and one or more other volumes included in the plurality of volumes;
determining, by the one or more computer processors based on the determining that the performance of the operation would affect the dependency between the volume and the one or more other volumes, that the request is possibly associated with a security threat against data stored on the volume by the storage system, wherein the determining that the performance of the operation would affect the dependency between the volume and the one or more other volumes is further based on an absence of a corresponding request to perform a corresponding operation with respect to the one or more other volumes; and
performing, by the one or more computer processors based on the determining that the request is possibly associated with a security threat, a remedial action with respect to at least one of the volume or a source of the request.
|