| CPC G06F 21/577 (2013.01) [G06F 21/552 (2013.01)] | 6 Claims |
|
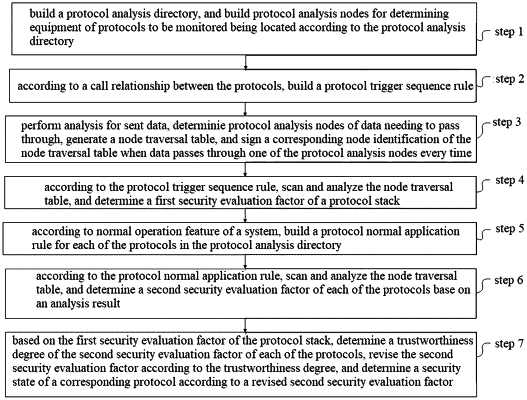
1. A security analysis method based on protocol state, comprising:
building a protocol analysis directory, and building protocol analysis nodes for determining equipment of protocols to be monitored being located according to the protocol analysis directory;
according to a call relationship between the protocols, building a protocol trigger sequence rule;
performing analysis for sent data, determining protocol analysis nodes of data needing to pass through, generating a node traversal table, and signing a corresponding node identification of the node traversal table when data passes through one of the protocol analysis nodes every time;
according to the protocol trigger sequence rule, scanning and analyzing the node traversal table, and determining a first security evaluation factor of a protocol stack;
according to normal operation feature of a system, building a protocol normal application rule for each of the protocols in the protocol analysis directory;
according to the protocol normal application rule, scanning and analyzing the node traversal table, and determining a second security evaluation factor of each of the protocols base on an analysis result;
based on the first security evaluation factor of the protocol stack, determining a trustworthiness degree of the second security evaluation factor of each of the protocols, revising the second security evaluation factor according to the trustworthiness degree, and determining a security state of a corresponding protocol according to a revised second security evaluation factor;
wherein based on the first security evaluation factor of the protocol stack, determining a trustworthiness degree of the second security evaluation factor of each of the protocols comprises:
setting a first security factor corresponding value array, and wherein the first security factor corresponding value array comprises a plurality of first security factor corresponding value intervals of being connected end to end, and each of the first security factor corresponding value intervals corresponds to a trustworthiness degree;
according to a first security factor corresponding value interval of the first security factor corresponding value belonging to, determining a trustworthiness degree of the second security factor;
wherein determining a security state of a corresponding protocol according to the revised second security evaluation factor comprises:
according to the revised second security evaluation factor, determining the security state value of the corresponding protocol, and wherein a expression of the security state value is determined as follows:
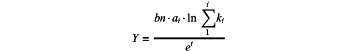 wherein, Y is the security state value, bn is a corresponding value of a second security evaluation factor of n-th protocol, ai is a corresponding value of a first security evaluation factor obtained after the protocol stack conforms to the protocol trigger sequence rule for i consecutive times, ki is a correction coefficient of the first security evaluation factor for i-th time, and t is a security expression parameter.
|