| CPC G06F 21/577 (2013.01) [G06F 2221/034 (2013.01)] | 12 Claims |
|
1. A system, comprising:
a processor;
a network interface in operable communication with the processor, the network interface operable for communicating with a network and providing the processor with access to information including common platform enumerations (CPEs) and corresponding common vulnerability enumerations (CVEs); and
a memory storing a set of instructions executable by the processor, the set of instructions, when executed by the processor, operable to:
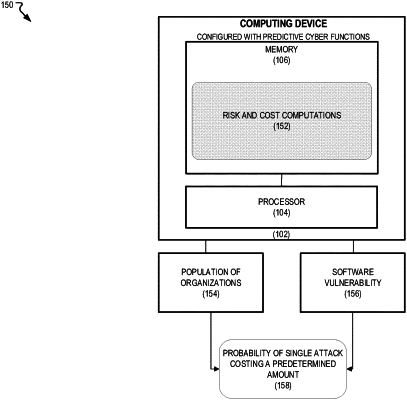
access a dataset, wherein the dataset comprises a plurality of vulnerabilities, a plurality of software components, and a plurality of organizations, wherein each of the plurality of organizations is associated with at least one of the plurality of vulnerabilities or at least one of the plurality of software components,
determine a set of risk probabilities using artificial intelligence for one of the plurality of software components or one of the plurality of vulnerabilities, wherein the set of risk probabilities comprises:
a first probability value associated with a probability that the software component or vulnerability will be exploited across the plurality of organizations, and
a second probability value associated with a probability that the software component or vulnerability in association with each of the plurality of organizations will be exploited,
evaluate a cost figure for the vulnerability or the software component based on the set of risk probabilities associated with the vulnerability or the software component and each of the plurality of organizations,
determine an overall probability that a software component or vulnerability will be exploited and have an associated payout of at least a given amount as a result of having been exploited across the plurality of organizations; and
after determining the overall probability, the processor is further operable to identify a first group of one or more organizations of the plurality of organizations such that one or more risk probabilities of the set of risk probabilities will be reduced if the corresponding vulnerability or software component is resolved.
|