| CPC G06F 16/2365 (2019.01) [G06F 21/552 (2013.01); G06F 21/566 (2013.01); G06F 21/6227 (2013.01); G06F 21/51 (2013.01); G06F 21/572 (2013.01)] | 20 Claims |
|
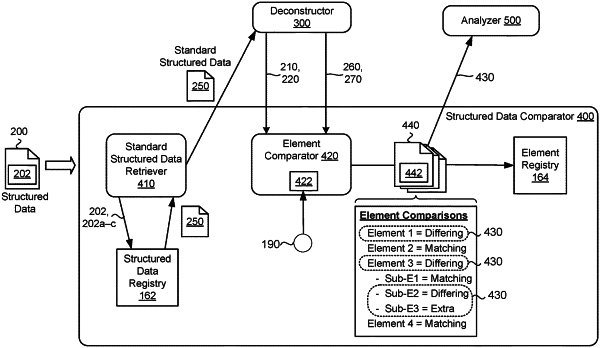
1. A computer-implemented method executed by data processing hardware that causes the data processing hardware to perform operations comprising:
obtaining a first element of structured data, the first element comprising a first value of an attribute;
receiving, for the first element of the structured data:
a standard element indicating a value of a master copy of the first element of the structured data; and
a tolerance indicating a threshold amount that the first element is allowed to deviate from the standard element;
comparing the first element to the standard element;
adjusting, based on the comparison of the first element to the standard element, the tolerance;
receiving a second element of structured data, the second element comprising a second value of the attribute;
determining, based on the adjusted tolerance, that second element satisfies the threshold amount that the second element is allowed to deviate from the standard element; and
in response to determining that the second element satisfies the threshold amount that the second element is allowed to deviate from the standard element, generating an alert indicating possible malicious activity.
|