| CPC H04L 63/145 (2013.01) [H04L 63/0428 (2013.01); H04L 63/1408 (2013.01); G06N 20/00 (2019.01)] | 20 Claims |
|
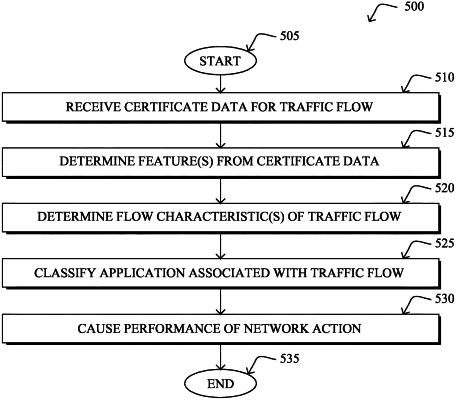
1. A method comprising:
obtaining, by a device in a network, certificate data of a presently encrypted traffic flow sent from a client node in the network to a remote server, wherein the certificate data of the encrypted traffic flow is passively intercepted by an intermediary device between the client node and the remote server without a man-in-the-middle;
determining, by the device, one or more data features from the certificate data of the encrypted traffic flow;
determining, by the device, one or more flow characteristics of the encrypted traffic flow;
performing, by the device, a classification of an application executed by the client node and associated with the encrypted traffic flow by using a machine learning-based classifier to assess the one or more data features from the certificate data of the encrypted traffic flow and the one or more flow characteristics of the encrypted traffic flow, wherein the machine learning-based classifier assesses the certificate data of the encrypted traffic flow without decrypting the encrypted traffic flow; and
causing, by the device, performance of a network action based on a result of the classification of the application.
|