| CPC G06Q 20/4016 (2013.01) [G06F 21/602 (2013.01); G06Q 20/382 (2013.01); H04L 9/008 (2013.01); H04L 9/0618 (2013.01); G06Q 2220/00 (2013.01)] | 20 Claims |
|
1. A method, comprising:
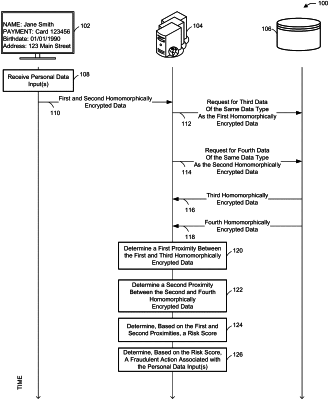
receiving, by at least one processor of a device, first data and second data, the first data and the second data being homomorphically encrypted, the first data comprising a name of a user, and the second data comprising at least one of a social security number or a payment account of the user;
retrieving, by the at least one processor, third data comprising name data, the third data being homomorphically encrypted;
retrieving, by the at least one processor, fourth data comprising at least one of social security number data or payment account data, the fourth data being homomorphically encrypted;
determining, by the at least one processor, a first proximity between the first data and the third data;
determining, by the at least one processor, a second proximity between the second data and the fourth data, wherein the first proximity and the second proximity are unassociated with an authentication using biometric data;
determining, by the at least one processor, based on a comparison of the first proximity to a first proximity threshold and based on a comparison of the second proximity to a second proximity threshold different than the first proximity threshold; a risk score associated with opening a user account based on the first data and the second data; and
identifying, by the at least one processor and based on the risk score, a fraudulent action associated with opening the user account based on the first data and the second data.
|