| CPC G06F 9/45558 (2013.01) [G06F 3/062 (2013.01); G06F 3/067 (2013.01); G06F 3/0662 (2013.01); G06F 16/1827 (2019.01); H04L 63/0869 (2013.01); G06F 2009/45562 (2013.01)] | 20 Claims |
|
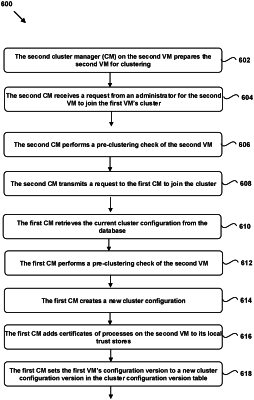
1. A method of adding one or more nodes to a first cluster including a first node in a computer system, the method comprising:
receiving, by the first node, a first request from a second node, the first request indicating an intention of the second node to join the cluster, wherein:
the first node is configured to execute a first one or more processes associated with one or more distributed applications;
the first request includes authentication information associated with the second node; and
the authentication information comprises one or more security certificates for a second one or more processes running on the second node;
retrieving, by the first node, a cluster configuration associated with the cluster from a database;
creating, by the first node, an updated cluster configuration using the cluster configuration and the authentication information;
populating, by the first node, a trust store associated with each of the first one or more processes with the authentication information to allow the first one or more processes to authenticate the second one or more processes running on the second node;
writing, by the first node, the updated cluster configuration to the database;
providing, by the first node, the updated cluster configuration to the second node;
determining, by a first process of the first one or more processes, that the first process can trust a second process of the second one or more processes based on retrieving, from the trust store associated with the first process, a corresponding security certificate of the one or more security certificates; and
communicating, by the first process, with the second process based on the determining that the first process can trust the second process.
|