| CPC G06F 21/64 (2013.01) [G06F 16/9014 (2019.01); G06F 21/602 (2013.01); G06Q 20/065 (2013.01); G06Q 30/0185 (2013.01); H04L 9/0637 (2013.01); H04L 9/0643 (2013.01); H04L 9/3236 (2013.01); H04L 9/3247 (2013.01); H04L 63/12 (2013.01); H04L 69/04 (2013.01); G06Q 2220/00 (2013.01); H04L 9/50 (2022.05); H04L 2209/56 (2013.01)] | 20 Claims |
|
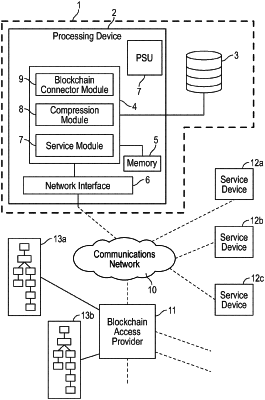
1. A computer-implemented method of tamper-evident recording of a plurality of service data items, each service data item being associated with a data item verification fingerprint, wherein a processing routine is conducted, in which
an aggregated verification fingerprint is computed from at least a plurality of data item verification fingerprints using at least one one-way compression function, so that the aggregated verification fingerprint has a bit length, which is less than a bit length of a concatenation of the data item verification fingerprints; and wherein
the aggregated verification fingerprint is stored in a plurality of blockchains for decoupling the storage of the aggregated verification fingerprint from the service data items;
the step of computing the aggregated verification fingerprint comprises computing a hash tree from the plurality of data item verification fingerprints;
for at least a first data item verification fingerprint of the plurality of data item verification fingerprints, a first authentication path comprising one or more hashes and a second authentication path comprising one or more hashes is determined in the hash tree, which first authentication path is associated with a branch path from the first data item verification fingerprint to the root hash in a first blockchain in which the aggregated verification fingerprint is stored, and which second authentication path is associated with a branch path from the first data item verification fingerprint in a second blockchain in which the aggregated verification fingerprint is stored;
the one or more hashes of said first authentication path are stored in a verification database;
the aggregated verification fingerprint is stored in at least a first block of the plurality of blockchains, wherein an identifier of the first block is stored in the verification database; and
the first data item verification fingerprint is stored in the verification database with the one or more hashes of said first authentication path and is correlated with the one or more hashes of said first authentication path.
|