| CPC G06F 21/604 (2013.01) [G06F 21/44 (2013.01); H04L 9/30 (2013.01); H04L 9/3226 (2013.01); H04L 9/3247 (2013.01); H04L 9/3268 (2013.01)] | 20 Claims |
|
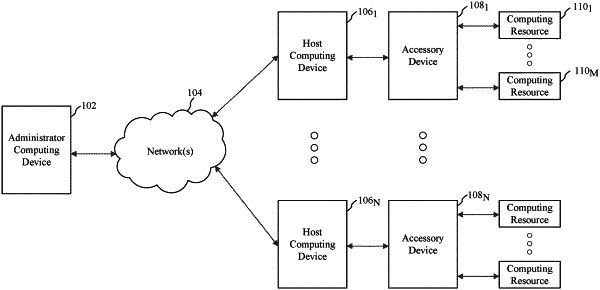
1. A method performed by an accessory device, comprising:
receiving a host access policy management command and authentication information from a host computing device that is connected to the accessory device, the host access policy management command indicating that a host access policy be set on, modified on, or removed from the accessory device, the host access policy specifying whether a host computing device that is subsequently connected to the accessory device is to be provided access to each of one or more computing resources accessible to the accessory device;
determining whether the authentication information is valid;
in response to at least determining that the authentication information is valid, executing the host access policy management command; and
in response to at least determining that the authentication information is not valid, denying execution of the host access policy management command.
|