| CPC G06F 21/335 (2013.01) [G06F 21/32 (2013.01); G06F 21/604 (2013.01); H04L 63/0227 (2013.01); H04L 63/107 (2013.01); H04L 67/141 (2013.01); G06F 2221/2105 (2013.01)] | 18 Claims |
|
1. A non-transitory computer readable medium including instructions that, when executed by at least one processor, cause the at least one processor to perform operations for passwordless authentication of a user, the operations comprising:
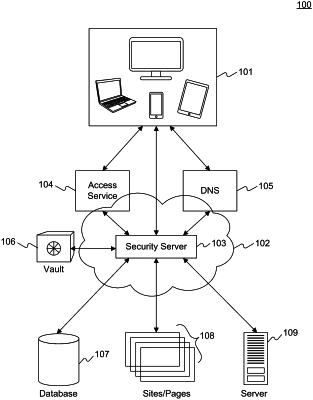
identifying a request by a user to access an access-restricted target resource, the user operating on a client computing device and the request being associated with a network address for the access- restricted target resource;
intercepting, by a security service in communication with a system server, the request before the request can reach the access-restricted target resource, wherein the
intercepting is based on a matching operation that compares the network address for the access-restricted target resource with one or more stored addresses, and includes the system server providing rerouting information for the request to an address associated with a security server; generating, by the security service, a unique session identifier, the unique session identifier being a one-time use identifier unique to the request and being generated in response to the request;
making available, through a computer-based user interface separate from the client computing device, the unique session identifier to the user of the client computing device, wherein the making available comprises at least one of displaying or audibly presenting a representation of the unique session identifier to the user;
and authenticating the user through a concurrent verification of an identity of the client computing device and a current physical presence of the user using sensor data, comprising:
generating a prompt for a physical verification of the user through the client computing device, the physical verification being based on one or more unique physical characteristics of the user and the sensor data, and performed entirely on the client computing device, receiving, from the client computing device concurrently with the physical verification, a decoded version of the unique session identifier that was made available to the user, the unique session identifier being returned through an action by the user on the client computing device as a result of the physical verification, and confirming the identity of the client computing device associated with the user, based on the received unique session identifier, the user's current physical presence at the client computing device, and the result of the physical verification;
and conditional on successful physical verification of the user and successful validation of the unique session identifier, establishing a secure tunnel connection between the client computing device and the access-restricted target resource.
|