| CPC H04L 63/1425 (2013.01) [H04L 41/16 (2013.01); H04L 43/04 (2013.01)] | 17 Claims |
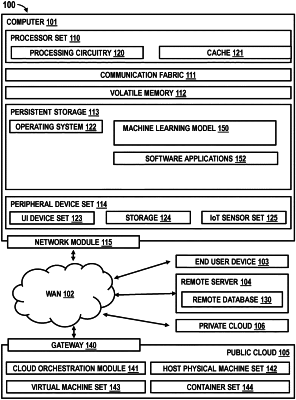
|
1. A computer-implemented method comprising:
receiving network traffic of a network;
extracting features from the network traffic, the features having a function related to communications in the network, wherein the features comprise a sequence of fully qualified domain names (FQDNs);
generating tokens from the features, each of the features corresponding to a respective one of the tokens;
training a machine learning model by inputting the tokens, the machine learning model being trained to output contextual embeddings for the tokens, wherein one or more of the tokens are masked by corrupting the one or more of the tokens during the training of the machine learning model; and
using the contextual embeddings to determine an anomaly in the network traffic.
|