| CPC H04L 63/0428 (2013.01) [H04L 9/0643 (2013.01); H04L 9/088 (2013.01); H04L 9/3215 (2013.01); H04L 9/3236 (2013.01); H04L 12/66 (2013.01); H04L 45/745 (2013.01); H04L 47/20 (2013.01); H04L 61/2592 (2013.01); H04L 61/5007 (2022.05); H04L 61/5038 (2022.05); H04L 2209/125 (2013.01)] | 16 Claims |
|
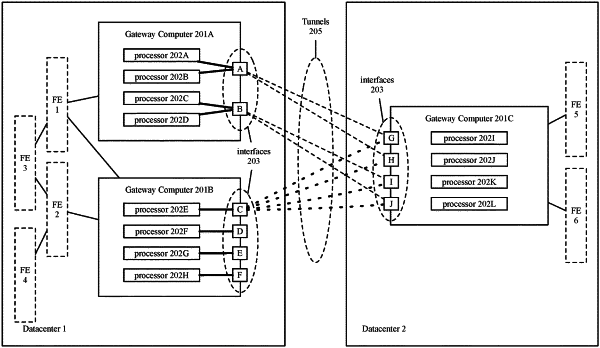
1. A method for processing a plurality of encrypted data messages sent over a plurality of encryption-secured tunnels using a plurality of data message processing units of a first computer in a first datacenter, each encryption-secured tunnel identified by a unique security parameter index (SPI), the method comprising:
at the first computer:
receiving the plurality of encrypted data messages through the plurality of encryption-secured tunnels established between the first computer and a second computer;
using an SPI of a particular encrypted data message to select a processing unit in the plurality of processing units to process the particular encrypted data message; and
using the selected processing unit to process the particular encrypted data message;
wherein the plurality of encryption-secured tunnels is a first plurality, a particular security policy is implemented by a second plurality of encryption-secured tunnels in the first plurality of encryption-secured tunnels, each of the second plurality of encryption-secured tunnels established between a different pair of interfaces of the first and second computers, a third plurality of encryption-secured tunnels in the first plurality of encryption-secured tunnels implement a plurality of security policies, each encryption-secured tunnel in the third plurality of encryption-secured tunnels established between a first interface of the first computer and second interface of the second computer.
|