| CPC G10L 15/22 (2013.01) [G06F 21/6254 (2013.01); G06F 40/279 (2020.01); G10L 15/26 (2013.01); H04L 9/0643 (2013.01); G10L 2015/223 (2013.01)] | 17 Claims |
|
1. A method, comprising:
receiving, at an input recognition system of an information handling device, text associated with a user command, wherein the text comprises an interpretation made by the input recognition system of the user command into a text transcription from an audible input provided by a user;
transmitting, responsive to the receiving, an indication of the text associated with the user command to a remote processing location, wherein the remote processing location receives indications of texts associated with user commands from a plurality of users;
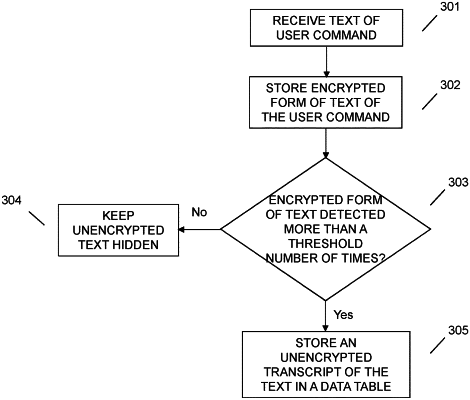
encrypting, responsive to determining the user command corresponds to a recognizable action and utilizing a hashing algorithm of an encryption technique, the text associated with the user command into an encrypted form, wherein the encrypted form comprises a hash value for a raw text of the command;
storing, in a data store comprising encrypted texts received from the plurality of users, the encrypted form of the text associated with the user command, wherein the storing the encrypted form of the text comprises storing a portion of the hash value of the text comprising the recognizable action corresponding to the user command, wherein identifying the recognizable action corresponding to the user command comprises accessing a data store of associations between user commands and associated actions;
determining, using a processor and based upon information stored within the data store, whether the encrypted form of the text has been detected in other user commands received from the plurality of users in exceedance of a predetermined threshold; and
storing, responsive to determining that the encrypted form of the text has been detected in the other user commands in exceedance of the predetermined threshold, an unencrypted transcript of the text in a data table visible to a user accessing the data table.
|