| CPC G06F 16/955 (2019.01) [G06F 16/9532 (2019.01); G06F 16/9538 (2019.01); G06F 18/22 (2023.01); H04L 41/0893 (2013.01)] | 20 Claims |
|
1. A method for processing network traffic by a network security appliance using a classification database of network devices, the method comprising:
identifying, by a processor, a host name of a connected network device on a network, wherein the host name indicates a type of network device;
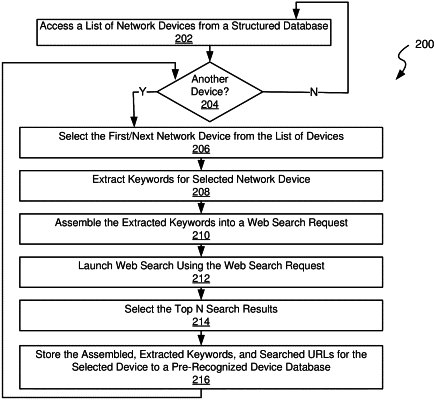
extracting, by the processor, at least a first keyword string indicating the type of network device from the host name;
launching, by the processor, a web search using at least the first keyword string to retrieve at least a first universal record locator (URL);
accessing, by the processor, a first pre-recognized network device record, wherein the first pre-recognized network device record indicates a first device type and includes at least a second URL;
calculating, by the processor, a similarity between the first URL and the second URL to yield a first similarity value;
accessing, by the processor, a second pre-recognized network device record, wherein the second pre-recognized network device record indicates a second device type and includes a third URL;
calculating, by the processor, a similarity between the first URL and the third URL to yield a second similarity value;
associating, by the processor, the connected network device with the first device type based at least in part on a comparison of the first similarity value and the second similarity value;
storing, by the processor, in a classification database an indication of the connected network device associated with the first device type; and
applying a network security rule to a continuing stream of network traffic from the connected network device, wherein the network security rule is selected based at least in part on the first device type identified in the classification database.
|