| CPC H04N 19/467 (2014.11) [H04L 9/0643 (2013.01); H04L 9/3249 (2013.01); H04N 19/176 (2014.11); H04L 2209/34 (2013.01); H04L 2209/608 (2013.01)] | 20 Claims |
|
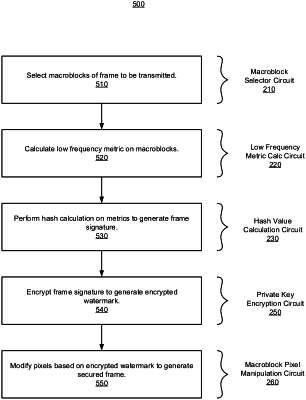
1. At least one non-transitory machine-readable storage medium comprising instructions to cause one or more processors to at least:
select a subset of macroblocks from a video frame to be transmitted;
generate a frame signature based on frame data associated with the video frame;
encrypt the frame signature to generate an encrypted watermark, the encryption based on a private key; and
modify modifying one or more pixels of ones of the subset of macroblocks based on bits of the encrypted watermark associated respectively with the ones of the subset of macroblocks to generate a secured video frame, the modification to include adjustment of one or more pixels of a first macroblock of the subset of macroblocks by one gray level to cause a least significant bit of an average of the one or more pixels of the first macroblock to correspond to a first bit of the encrypted watermark that is associated with the first macroblock.
|