| CPC H04L 9/088 (2013.01) [H04L 9/0894 (2013.01); H04L 9/50 (2022.05)] | 21 Claims |
|
1. A computer-implemented method, comprising:
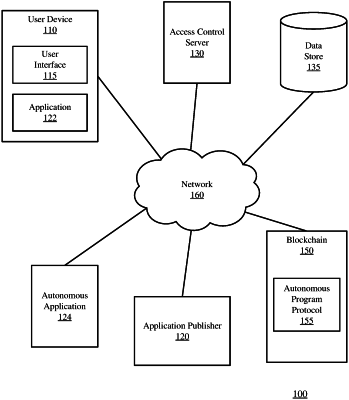
storing a private cryptographic key outside of a blockchain and in an access control server, the private cryptographic key belonging to the access control server, wherein the private cryptographic key corresponds to a public cryptographic key, a copy of the public cryptographic key is stored on the blockchain in a smart contract that is recorded on the blockchain;
receiving, by the access control server, an access control setting related to the smart contract, the access control setting specifying one or more policies in granting access to the smart contract;
receiving a plurality of requests for accessing the smart contract stored on the blockchain, the plurality of requests comprising a first request from a first user and a second request from a second user, the first user being different from the second user;
determining, for each of the plurality of requests, whether the request is in compliance with the one or more policies specified in the access control setting, compliant requests comprising the first request and the second request;
creating, by the access control server using the private cryptographic key, a first digital signature of the access control server and a second digital signature of the access control server, the first digital signature verifying the first request from the first user and the second digital signature verifying the second request from the second user;
generating a first response to the first request, the first response comprising the first digital signature of the access control server, wherein the smart contract, in response to receiving the first digital signature, verifies the first digital signature using the public cryptographic key stored in the smart contract, and wherein a first successful verification of the first digital signature is required by the smart contract to process the first request from the first user; and
generating a second response to the second request, the second response comprising the second digital signature of the access control server, wherein the smart contract, in response to receiving the second digital signature, verifies the second digital signature using the public cryptographic key stored in the smart contract, and wherein a second successful verification of the digital signature is required by the smart contract to process the second request from the second user.
|