| CPC H04L 9/004 (2013.01) [H04L 9/0869 (2013.01); G06F 7/588 (2013.01); H04L 2209/08 (2013.01); H04L 2209/12 (2013.01)] | 18 Claims |
|
9. A non-transitory computer-readable medium or media comprising one or more sequences of instructions which, when executed by at least one processor, causes steps to be performed comprising:
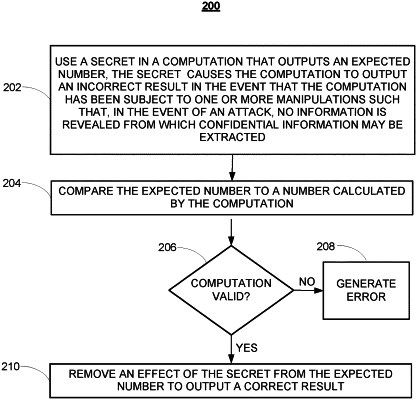
using a secret in a computation that outputs an expected number, the secret causes the computation to output an incorrect result in the event that the computation has been subject to one or more manipulations such that, in the event of an attack, no information is revealed from which confidential information may be extracted;
comparing the expected number to a number calculated by the computation;
based on the comparison, determining whether the computation is valid;
in response to the computation being invalid, generating an error indicating that the computation has been subject to the one or more manipulations; and
in response to the computation being valid, removing an effect of the secret from the expected number to output a correct result.
|