| CPC H04L 63/20 (2013.01) [G06F 21/57 (2013.01); G06F 21/604 (2013.01); G06F 21/6218 (2013.01); H04L 63/08 (2013.01); H04L 63/10 (2013.01); H04L 63/102 (2013.01); H04L 63/1408 (2013.01); G06F 9/54 (2013.01)] | 20 Claims |
|
1. A processor-based system comprising:
memory; and
a processing system coupled to the memory, the processing system configured to:
detect that an identified access control policy is created and set to an enforcement state in which the identified access control policy is to be enforced;
provide a warning that recommends simulating enforcement of the identified access control policy with regard to an identified actual sign-in process instead of enforcing the identified access control policy with regard to the identified actual sign-in process;
detect that a state of the identified access control policy is changed from the enforcement state to a simulation state in which the enforcement of the identified access control policy with regard to the identified actual sign-in process is to be simulated;
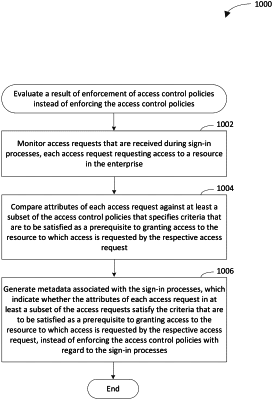
simulate enforcement of access control policies, including the identified access control policy, with regard to actual sign-in processes that are configured to sign-in users to a system instead of enforcing the access control policies with regard to the actual sign-in processes by performing operations, the operations comprising:
monitor access requests that are received during the actual sign-in processes, the access requests requesting access to a resource in the system;
compare attributes of the access requests against at least a subset of the access control policies that specifies criteria that are to be satisfied as a prerequisite to granting access to the resource to which access is requested by the access requests; and
generate metadata associated with the actual sign-in processes, which indicate whether the attributes of the access requests in at least a subset of the access requests satisfy the criteria that are to be satisfied as a prerequisite to granting access to the resource to which access is requested by the access requests, instead of enforcing the access control policies with regard to the actual sign-in processes; and
provide a recommendation, which recommends performance of an action, based at least in part on simulation of the enforcement of the access control policies with regard to the actual sign-in processes and based at least in part on the attributes of a specified access request not satisfying the criteria that are to be satisfied as the prerequisite to granting access to the resource to which access is requested by the specified access request.
|